Quiet But Deadly – Understanding Silent PC Killers Threatening Ithaca, NY’s Business Environment
Are you a victim or survivor of silent PC killers silently targeting your desktop or laptop devices? It’s high time to address the lingering issues in your hardware and software-related systems before they gradually become a ticking time bomb of problems. In today’s digital age in Ithaca, NY, and across the globe, businesses heavily depend on desktop or laptop devices for their daily work operations. However, many unintentionally ignore the silent killers, such as excessive noise, corrupt hard drives, dust buildup, and malware lurking.
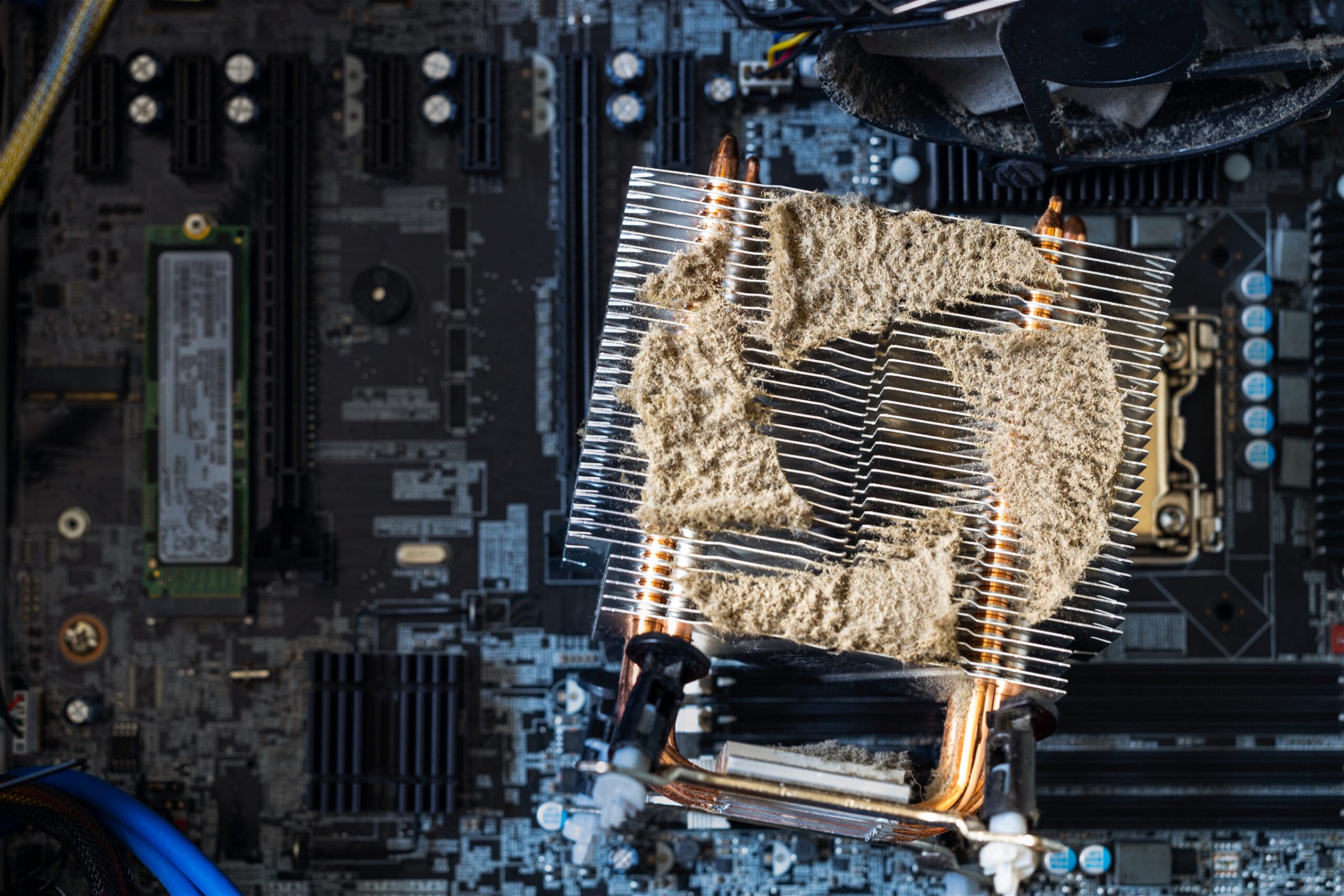
Cooling is a critical aspect of common computer issues that often slip under the radar until faced with a downtime crisis. Monitoring this can lead to the dreaded blue screen or noisy machine glitches. In most cases, dust and debris accumulated over a long period in external devices can cause overheating, leading to slower performance and even complete system failure. Using efficient HDD vibration killers in the assembly phase can help survivors avoid this frustrating scenario.
Beyond physical damage, these silent killers can pose severe threats to data security, presenting a grave risk to your operations. Dead vibrations can also affect the performance of external devices like hard drives, raising a red flag for businesses needing to rely on their computer systems for an extended period.
Businesses need an idea of these looming threats, such as dead cases and faulty systems, and make immediate improvement plans. Simple things like neglecting the cooling system and failing to rectify common computer problems such as dust, cases, and drive issues can expose a business. Ensuring your hardware works correctly with a feasible cooling system and employing HDD vibration killers can provide a solid defense against these silent killers.
In this article, we will explain the importance of an efficient HDD vibration killer, compel the need for immediate action against silent killers, and create urgency to help survivors and businesses in Ithaca & Central New York protect themselves from these hidden dangers.
Why (Silent) Hardware Threats Often Go Unnoticed
Like everywhere else, most businesses in Ithaca, New York, focus more on software threats such as viruses, malware, and phishing attacks. However, it’s equally vital not to overlook the physical or hardware issues that can harm your computer.
Dust is a common computer problem that develops into a big problem over time. This seemingly harmless dirt inside your computer case can cause damage to the internal hardware components. Systems can load slower when coated in dirt and dust; most issues arise from this silent killer. Regular cleaning of fans, vents, and even the keyboard can protect hardware from such threats.
Then, there’s the not-so-obvious threat of vibration, often a hardware issue that can develop from nearby construction or heavy machinery. These vibrations can give your hard disk a hard time, leading to potential data loss or system failure. These are common hardware problems, and it’s necessary to take note of these threats.
To prevent silent PC killers like these, you must watch every side of your hardware and be privy to issues like hard drive vibration, which could signal a potential HDD killer. Caused by factors such as proximity to a construction site or an internal battery or fan’s vibration, these silent threats can wreak havoc if left unattended. So, how can they fly under the radar, you ask?
Silent PC killers camouflage themselves by exploiting the stealthy nature of vibrations and drives, evading detection while impacting the functionality of desktops and laptops. Their covert means of operation make them a difficult enemy to tackle, but the proper steps, like a regular system restart or virus scan, help to keep them at bay.
Contrary to the belief that a slow-loading system might just need unnecessary programs removed or to uninstall drivers, the problem could point out a vibration killer at work. Herein lies the significance of an HDD Vibration Killer. This device becomes a shield, safeguarding your system from potentially corrosive vibrations and tackling multiple threats simultaneously – a perfect idea for those looking for comprehensive solutions.
These silent threats pose a significant risk, and businesses and individuals must remain especially vigilant. With awareness comes the power to tackle these hardware threats and safeguard essential software or hardware assets.
Highlighting the Lack of Awareness and Understanding Among Businesses
Despite the increasing sophistication of hardware threats, many businesses still lack awareness and understanding regarding this critical aspect of cybersecurity. Protecting sensitive data stored on hard drives is one area often overlooked. Implementing a reliable drive encryption solution can help prevent unauthorized access to data while using a vibration killer can safeguard against physical damage to hard drives.
The primary focus has been software-based attacks due to their prevalence in public discourse and media coverage. However, it is essential not to neglect the significance of physical security measures, such as drive encryption and vibration-killer technology. As a result, organizations often allocate more resources towards protecting against software threats while neglecting potential vulnerabilities at the hardware level, such as the vibration killer.
Businesses must recognize that overlooking hardware threats, such as vibration killers, puts them at significant risk. It only takes one compromised device, a vibration killer, to expose an entire network and compromise sensitive data. Raising awareness about the existence and potential impact of silent PC killers, such as vibration, is crucial to ensure that organizations take necessary precautions to safeguard their hardware infrastructure.
The Dangers of Neglecting the Hidden Threats of Silent PC Killers
In today’s digital age, where businesses heavily rely on computers and technology, it is crucial to be aware of the hidden threats of silent PC killers. These unnoticed dangers, such as vibration killers, can have severe consequences if neglected. Let’s delve into the potential risks and outcomes associated with overlooking hardware threats, emphasizing the need for proactive measures to mitigate these dangers.
One significant danger of ignoring silent PC killers is the financial losses that businesses may incur. Hardware threats such as HDD vibration killers can cause damage to computer components over time. The constant vibrations generated by these devices can lead to hard disk drive failure, resulting in data loss and expensive repairs or replacements. This damage could be disastrous for small businesses or individuals who lack proper backup systems, potentially leading to irretrievable data loss and substantial financial setbacks.
Data breaches are another grave consequence that can arise from neglecting silent PC killers. Cybersecurity threats like software vulnerabilities, external hackers, or internal hardware issues should not be underestimated when combatting data breaches. A dead fan or faulty power supply can cause overheating within a computer system, increasing the risk of compromised sensitive data due to unexpected shutdowns or system failures.
Moreover, reputational damage is a significant concern. In today’s interconnected world, news spreads rapidly through social media platforms and online reviews. If a business experiences frequent disruptions due to hardware failures caused by neglecting silent PC killers, customers may lose trust in its ability to provide reliable services or protect their confidential information. This loss of reputation could result in decreased customer loyalty and even potential legal repercussions if negligence is proven.
When mitigating these dangers, proactive measures must be taken seriously. Businesses should prioritize addressing silent PC killers by implementing regular maintenance schedules for their computer systems. These measures include monitoring hardware performance indicators such as temperature levels, fan speeds, and overall system health.
Investing in top-quality hardware and ensuring proper ventilation within computer setups can significantly reduce the risk of silent PC killers. Utilizing specialized tools such as HDD vibration killers or noise-dampening materials can minimize vibrations and noise generated by computer components, prolonging their lifespan and reducing the likelihood of failures.
How Silent PC Killers Affect the Finances of Businesses in Ithaca, New York
Hardware threats can have a significant financial impact on businesses, causing unexpected expenses and disruptions to normal operations. These silent PC killers affect the performance and reliability of computer systems and lead to increased costs that can strain a company’s finances.
One significant consequence of hardware threats is the need for increased maintenance. When PCs are compromised by viruses, malware, or faulty hardware, businesses often have to invest in regular repairs and replacements. This constant cycle of fixing issues can quickly add up, draining resources that could be better allocated elsewhere.
Discussing Increased Maintenance Costs and Decreased Productivity Due to System Failures
When PCs fail due to silent killers like overheating components or hard drive failures, businesses face repair costs and decreased productivity. Employees cannot carry out their tasks efficiently or complete projects on time when their computers are constantly crashing or experiencing slow performance.
The financial implications of reduced productivity should be considered. Delays in project completion can result in missed deadlines and dissatisfied clients, potentially leading to lost business opportunities. Moreover, employees’ frustration with malfunctioning PCs may negatively impact morale and job satisfaction, further affecting overall productivity.
Addressing Potential Revenue Loss Resulting From Downtime or Data Breaches
Silent PC killers pose another threat that can directly impact a company’s bottom line: downtime and data breaches. When computer systems become compromised, or experience extended downtime due to hardware issues, businesses lose valuable working hours that could have been spent generating revenue.
Furthermore, data breaches resulting from security vulnerabilities in PCs can have severe financial consequences. The cost of recovering compromised data, notifying affected customers, dealing with legal repercussions, and rebuilding trust with clients can be substantial. Reputational damage from a breach may deter potential customers from doing business with the affected company.
Emphasizing that Investing in Prevention is More Cost-effective than Dealing with the Aftermath
The adage’ prevention is better than cure’ holds even in protecting businesses from silent PC killers. While these covert threats might have substantial financial implications, prudence lies in recognizing the long-term cost-effectiveness of investing in preventive measures.
Experiencing a hardware system failure or data breach due to these silent threats is often followed by costly solutions – leading to expenditure on emergency IT support, data recovery, hardware replacements, and, in extreme cases, fines related to data breaches. These incidents also affect a business’s productivity, customer trust, and, potentially, their market reputation.
In contrast, investing proactively in the preventive arena – from regular system inspections timely hardware and software upgrades to a robust cybersecurity framework and consistent staff training – pays off substantially. It facilitates early detection and quick action, minimizing the risk of severe disruptions.
In adopting this approach, businesses safeguard their essential functionality from potential silent PC killers, conserve financial resources, and efficiently secure their long-term interests. After all, when it comes to ensuring the smooth operation of your IT infrastructure, an ounce of prevention is worth a pound of cure.
Know the Enemy: Identifying the Varying Sources of Silent Hardware Threats For Ithaca, NY, Businesses
Silent PC killers can lurk in many forms, some being the most common problems businesses across Ithaca, NY, face. Let’s dissect these sources to safeguard your Windows PC and prevent potential damage proactively.
Dust Accumulation: A Shadowy Menace Hidden in the Daylight
A dusty computer case might seem innocuous, but it becomes a secret assassin when it gathers inside your PC. The poor mounting of components like fans, heatsinks, stock drive cage units, or Wi-Fi adapters impedes proper airflow and causes overheating, slowing down your Windows interface.
Power Surges: A Shocking Hardware Threat
Power surges seriously blow your hardware, posing a big problem over time. One precautionary measure is investing in reliable power supplies and good power cable management. The placement of a surge protector can guard your desktop and laptop devices against this silent threat, ensuring they survive and continue working correctly. In the same vein, proper operation and maintenance of the power button may seem trivial, but it is indeed an essential step in managing these menaces.
The power button not only allows the machine to boot up but also serves as a primary fix for many common computer problems: a quick reset can often resolve minor hitches, unexpected freezes, or even load issues in the operating system. Yet, if constantly mishandled or excessively used, the power button itself may encounter wear and tear, which can add up to the most trivial but annoying hardware issues.
Aging Components and Driver Issues: Slow and Steady Decay
Monitoring component lifespans and replacing aging parts is crucial for optimal OS performance, such as Windows, Linux, Mac, or other operating systems. Graphics drivers need frequent updates to ensure smooth visual output. In contrast, hard disk drives might need replacements or upgrades as time passes. Keyboard issues may arise over time, which block data lines or cause unnecessary interruptions. Using the control panel for updates and fixes can help keep these silent killers at bay (accessible from the start menu on Windows devices).
Malware-Infected Devices: An Unseen Threat across Windows Devices
Malware-infected networks and devices, for example, an infected Wi-Fi connection, pose a significant threat to hardware systems. Though these silent killers can bring severe computer issues, implementing robust security measures like firewalls, antivirus software, and regular network scans can detect and neutralize them.
Defending Against Malintent: Internal & External Threats to Hardware Systems
Success in ensuring the reliability of your hardware systems calls for an in-depth understanding of the potential threats it might face. In information technology, these threats fall into two primary classifications: internal and external. Each carries its unique challenges and requires a distinct approach for effective defense.
Internal threats often originate from within the system itself, and usually, they are unintentional. They could involve hardware failure, outdated software, misconfiguration, or, in some cases, be a consequence of actions by untrained or negligent employees. Malfector individuals or entities outside your organization often orchestrate these threats. These often maliciously intended threats can range from malware attacks, hacking attempts, and phishing schemes to large-scale distributed denial-of-service attacks.
Being vigilant against these threats while distinguishing between them paves the path toward a more resilient hardware system. Constant vigilance enables businesses to deploy precise and swift interventions whenever these silent PC killers rear their heads, ultimately safeguarding business operations and sensitive data.
In the upcoming section, we will delve deeper into the differential aspects of internal and external threats while offering timely and practical measures for their prevention and control.
Differentiating Between Internal and external Threats to Hardware Systems
Internal threats refer to risks that arise from within an organization or company. Disgruntled employees or unauthorized individuals may attempt to access sensitive information or intentionally cause harm to hardware systems. These individuals might exploit their knowledge of the system’s weaknesses or vulnerabilities, posing a significant threat.
On the other hand, external threats originate from outside sources. Hackers, malware, and phishing attempts fall under this category. Cybercriminals constantly seek opportunities to breach hardware systems for financial gain or malicious intent.
Discussing the Risks Posed by Disgruntled Employees or Unauthorized Access
Disgruntled employees can pose a severe risk to hardware systems due to their insider knowledge and potential motivation for sabotage. They may intentionally introduce malware into the system, steal sensitive data, or disrupt critical operations. Unauthorized access by individuals who do not have legitimate permissions also poses a similar risk.
Organizations should implement strict access controls to mitigate these risks and regularly review user privileges. Limiting access only to those who require it for their specific roles and responsibilities is essential. Monitoring tools can help detect any suspicious activities within the system promptly.
Addressing External Threats Like Hackers, Malware, and Phishing Attempts
Hackers are constantly evolving their techniques in an attempt to breach hardware systems. They exploit vulnerabilities in software programs or network infrastructure to gain unauthorized access. Once inside the system, they may steal valuable data or compromise its functionality.
Malware refers to malicious software designed to cause harm or gain unauthorized access. It includes viruses, worms, ransomware, and spyware. These threats can enter a hardware system through various means, such as email attachments, infected websites, or compromised software downloads.
Phishing is a cyber threat where attackers masquerade as trustworthy entities to trick individuals into revealing sensitive information like passwords and credit card numbers. Phishing is achieved through convincingly designed emails or messages that create urgency or fear, prompting hasty responses.
These deceptive messages often link to fake websites where users are tricked into providing their information or may contain attachments that secretly deploy malicious software onto the user’s device. As phishing commonly targets human vulnerability rather than technology, fostering awareness and caution forms the best defense against such threats.
System Deterioration: How Common Computer Problems Develop Over Time
Computers are remarkable machines that have become an integral part of our lives. They enable us to accomplish numerous tasks efficiently and effortlessly. However, it is essential to acknowledge that these technological marvels are not immune to the effects of time. Computers undergo a natural degradation process throughout their lifespan, which can significantly impact their performance and longevity.
Explaining the Natural Degradation Process of Computer Hardware Over Time
As with any physical object, computers are susceptible to wear and tear. The constant use, movement, and handling gradually take a toll on their components. Hard drives, for instance, experience vibrations during operation, leading to mechanical failures over time. This deterioration becomes more pronounced as the computer ages.
Discussing Factors Such as Wear and Tear, Heat Buildup, and Component Aging
Heat buildup is another silent killer that affects computer systems. As we rely on our computers for extended periods, they generate heat due to continuous processing. Overheating can cause severe damage to delicate components such as the central processing unit (CPU) or graphics card (GPU). Moreover, high drive temperatures can lead to data corruption or even complete drive failure.
Component aging also plays a significant role in system deterioration. Electronic parts have a limited lifespan influenced by usage patterns and environmental conditions. Capacitors are particularly vulnerable to aging; they may dry out or leak electrolyte fluid over time, compromising the entire system’s stability.
Highlighting the Importance of Regular Maintenance and Monitoring to Prevent System Deterioration
When mitigating these issues effectively, regular maintenance is essential. Cleaning your computer from accumulated dust and dirt ensures proper airflow and prevents overheating. Using compressed air or specialized cleaning tools for electronic devices is advisable.
Monitoring your computer’s temperature is equally crucial. Various software applications allow you to check CPU and GPU temperatures in real-time so that you can take appropriate action if they exceed safe limits. Monitoring hard drive health and performing regular disk checks can help identify potential issues before they escalate.
Encouraging Businesses to Schedule Routine Inspections and Upgrades
In the fast-paced digital landscape that businesses operate in today, a well-maintained and up-to-date computer system isn’t just an asset; it is a necessity. The bedrock of smooth operations and seamless productivity often rests on the functionality and efficiency of these systems. That’s why routine inspections and timely upgrades should be a cardinal part of any business’s IT strategy.
Routine inspections involve thorough checks of the system’s hardware and software components. Inspections can help catch potential issues well before they escalate into disruptive problems. Whether identifying aging hardware before it fails or detecting irregular system behaviors that could hint towards a potential virus or malware, a thorough inspection can keep a business ‘in the know’ and ‘in control’ of its IT environment.
Equally important are frequent upgrades, which are crucial for staying ahead of the curve. Software upgrades provide enhanced features and patch potential security vulnerabilities, ensuring your systems remain robust against emerging threats. Hardware upgrades, while often overlooked, play a vital role in maintaining the speed and reliability of the system, directly influencing business productivity.
Businesses must be bold in this dynamic and evolving cyber landscape. Proactively scheduling routine inspections and necessary upgrades is a business’s first defense against silent PC killers, effectively safeguarding its operations, reputation, data, and bottom line.
Staying Steps Ahead: Proactive Measures to Detect Silent PC Killers
In today’s fast-paced digital landscape, staying steps ahead in detecting silent PC killers is crucial for businesses and individuals alike. These invisible threats can wreak havoc on computer systems, causing hardware failures, data loss, and productivity setbacks.
Safeguarding against these insidious dangers involves essential proactive detection practices. Here, we will explore the significance of such measures and provide practical tips to help you stay ahead in the game.
Monitoring Software: Identifying Potential Hardware Issues Early On
One effective way to detect silent PC killers is by utilizing monitoring software. This powerful tool lets you closely monitor your system’s performance and identify potential hardware issues before they escalate into major problems. You can catch warning signs early by monitoring critical components such as CPU temperature, fan speed, and hard drive health.
Understanding and Safeguarding Your USB Port
The USB port is more than just a connector; it’s the vital bridge that allows your device to communicate and connect with many external devices. As businesses use these ports unlimited times, it becomes an important yet vulnerable aspect of your hardware system.
USB ports are more susceptible to physical damage and data breaches, primarily when used carelessly in the hustle and bustle of business operations across Ithaca & Central New York. Hence, safeguarding the integrity of your USB ports is essential and begins with understanding their capacity and potential vulnerabilities.
Mastering Device Manager for Optimal PC Health
One profoundly undervalued tool in maintaining optimal PC health is the device manager. Integral to the Windows operating system, it simplifies troubleshooting common computer problems. It allows you to monitor and control the hardware attached to your system, including managing your USB ports, among other devices; effectively, it’s your built-in task manager for hardware.
By mastering how to navigate and effectively use the device manager, businesses from the broader region can ensure their hardware systems – from the simple USB port to more complex components – are working correctly and quickly address any issues. Regular use and understanding of this tool can take you one step further in safeguarding your hardware from silent PC killers.
Regular System Scans, Diagnostic Checks, Operating System Updates, and Performance Evaluations
Regular system scans, diagnostics, and performance evaluations are other proactive measures that should be integral to your PC hygiene routine. Conducting thorough scans using reliable antivirus software helps detect hidden malware or viruses that may silently compromise your system’s integrity. Running diagnostic tests can illuminate any underlying hardware issues that require attention.
The Benefits of Proactive Detection Methods
Opting for proactive detection methods has far-reaching advantages, rooted in averting disastrous computer systems’ failures and ensuring their optimal functionality and longevity. Here’s a more comprehensive look at their benefits:
Minimization of Disruptive Risks: In an era where businesses significantly depend on technology, abrupt hardware crashes can cause a ripple effect of disruption, from halting your workflow to necessitating expensive repairs. Proactive detection greatly reduces these potential risks, keeping business operations running smoothly.
Promotion of Preventative Measures: The value of early problem identification within any system cannot be overstated. Proactive detection brings issues to the fore, facilitating immediate intervention. This approach allows for an efficient “nip the issue in the bud” strategy that prevents small issues from becoming significant problems – saving time, effort, and resources.
Enhancement of System Performance: Crucially, keeping a watchful eye on the health status of your computer system can significantly enhance its performance. Systems running with undetected issues will often underperform, hinder productivity, and cause user frustration. By detecting and fixing issues proactively, peak performance is maintained, leading to more efficient and satisfying user experiences.
Extension of System Lifespan: Proactive detection is not just about solving the issues of today, but also preserving for the future. By continuously ensuring that all system components are functioning effectively, the overall lifespan of the computer system is extended. In the long run, this contributes to cost savings via reduced frequency of hardware replacements.
Reputation Protection: For businesses, system failure can lead to disastrous consequences, ranging from dissatisfied customers to lost sales and tarnished brand reputation. Proactive detection aids in avoiding such situations, helping to maintain a strong market standing.
By integrating proactive detection methods into your technical administrative routines, you can enjoy a seamless, efficient, and productive digital experience.
Multiple Ways for Businesses to Stay Ahead in Detecting Silent PC Killers
For businesses dealing with multiple computers interconnected within a network environment, staying ahead in detecting silent PC killers becomes even more critical. Here are some strategies businesses can adopt:
- Centralized Monitoring: Implement a centralized monitoring system that provides real-time insights into the health and performance of all connected devices, enabling swift detection of any anomalies.
- Regular Maintenance Schedule: Establish a regular maintenance schedule where system scans, software updates, and hardware checks are performed at predefined intervals to ensure optimal functioning.
- Staff Training: Educate your team about the tell-tale signs of potential hardware threats. These signs range from unusual system noises, slow performance, frequent crashes, or files becoming corrupt unexpectedly. The sooner these signs are recognized and reported, the quicker action can be taken.
- Invest in Cybersecurity Measures: Cybersecurity measures like firewalls, antivirus software, and intrusion detection systems can help identify and neutralize threats. Regularly updated cybersecurity tools can protect against new malware, ransomware, and other silent PC killers.
- Data Backup and Recovery Plan: Regularly backing up critical data ensures businesses can restore their operations with minimal disruption, even when a severe hardware failure occurs. Make the data backup and recovery plan part of your strategy against silent PC killers.
- Up-to-date Inventory: Keep an up-to-date inventory of all computer hardware and monitor each device’s end-of-life. Upgrading old hardware in time prevents system failures and possible data loss, which are common business impacts of silent PC killers.
- Consult IT Experts: Regular consultations with IT professionals can help identify potential threats and develop strategies tailored to the business’s needs. They can provide a thorough, well-rounded assessment of your current IT environment and guide your business toward the best preventative measures.
- Implement Power Management: Connect all systems to power surge protectors and have a backup power supply. This measure can protect your hardware from power-related silent PC killers like voltage spikes or accidents that can cause system outages.
By implementing these strategies, businesses can stay ahead of the silent threats that can compromise their hardware, leading to improved business operations, protected data, and saved costs.
The Next Steps: Seeking Professional IT Support to Avoid Silent Killers
In today’s digital age, businesses heavily rely on computers and technology for their day-to-day operations. However, hidden dangers are lurking within these machines that can silently wreak havoc if left unchecked. These silent PC killers pose a significant threat to the smooth functioning of any organization. To effectively address these issues, businesses must seek professional IT support.
Seeking expert advice and assistance is paramount. Professionals in the field possess the necessary knowledge and experience to assess vulnerabilities within your system and provide appropriate solutions. Through rigorous testing, they can identify potential weak points that may be exploited by malicious actors or overlooked by inexperienced individuals.
One of the key advantages of engaging professional IT support is their ability to implement preventive measures. They fix existing issues and proactively safeguard your systems from future threats. Regularly monitoring your hardware and software ensures comprehensive protection against silent killers that could cause irreparable damage.
Finding reliable IT support services in Ithaca, NY, may seem like a daunting task, but there are several avenues you can explore:
- Seek recommendations from local businesses that have successfully dealt with silent PC killers.
- Conduct online research and read reviews from reputable sources to gauge the quality of service provided.
- Contact industry associations or trade groups for referrals to trusted IT professionals.
- Consider consulting with local technology experts who specialize in addressing hardware threats.
Once you have identified potential IT support providers, evaluating them based on their expertise and track record in dealing with silent PC killers is essential. Look for successful cases where they have helped businesses improve their systems’ resilience against such threats.
Malware that Poses A Threat to Your Business Hardware
Malware is not just a software problem; it can also wreak havoc on your hardware systems. A rootkit is one of the most dangerous types of malware that can cause significant damage to your hardware. Rootkits are malicious programs designed to gain unauthorized access to a computer system by exploiting security vulnerabilities.
Once installed, they embed themselves deep within the operating system, making them difficult to detect and remove. Rootkits can take control of various hardware components, compromising the overall security of your business machines.
Another type of malware that poses a serious threat to business hardware is firmware attacks. Firmware is the software code embedded in hardware devices such as motherboards or hard drives. Attackers exploit vulnerabilities in firmware to gain unauthorized access or control over these devices, potentially leading to data breaches or complete device compromise. Firmware attacks often go unnoticed since they occur at a level deeper than traditional antivirus software can detect.
Robust antivirus software and regular updates are essential to protect your business from these silent PC killers. Antivirus software scans for known malware signatures and behavior patterns while providing real-time protection against emerging threats. Regular updates ensure your antivirus program has the latest virus definitions and security patches for detecting and neutralizing new malware strains.
In addition to antivirus software, there are other preventive measures you can take:
- Implement a robust security configuration: Configure your business machines with secure settings and permissions, minimizing potential vulnerabilities.
- Keep all operating systems and applications up-to-date: Regularly install updates and patches provided by manufacturers to address any identified security flaws.
- Educate users about safe browsing habits: Train employees to recognize phishing attempts, suspicious websites, or email attachments that may contain malware.
- Secure physical access to hardware: Protect your business machines by securing them in locked cabinets or rooms, limiting unauthorized physical access.
- Use tamper-proof screws and rubber bays: Prevent physical tampering with your hardware by using screws that require special tools and rubber USB-C bays to seal off unused ports.
How to Recover From Hardware Failure: From Data Backups to Component Repair
Regular data backups are crucial for businesses to recover from hardware failures effectively. Hard drives can fail unexpectedly, leading to potential data loss. By backing up critical data regularly, businesses can minimize the impact of hardware failures and ensure that critical information is not lost.
Off-site storage is an essential aspect of data backup strategies. Storing backups in a separate location ensures that even if the primary hardware fails or is damaged, the backups remain safe and accessible. Cloud-based solutions offer convenient off-site storage options, providing businesses with secure and reliable backup solutions.
To implement adequate data backups and off-site storage:
- Identify critical data: Determine which files, documents, databases, or applications are vital for business operations.
- Choose a backup method: Select a suitable backup method based on the needs of your business. External hard drives, network-attached storage (NAS), or cloud-based services are options.
- Set up automatic backups: Schedule regular automated backups to ensure consistent critical data protection.
- Verify backup integrity: Periodically test your backups by restoring them to ensure they are complete and functional.
- Store backups off-site: Utilize cloud storage services or physically store backups in a secure location away from the primary hardware.
Component Repair or Replacement When Necessary
When faced with hardware failure, assessing whether component repair or replacement is the best course of action is essential. Depending on the severity of the failure and cost considerations, repairing specific components may be more feasible than replacing them entirely.
Consider these factors when deciding between repair or replacement:
- The severity of damage: Evaluate the damage’s extent and whether it’s fixable through repairs.
- Cost-effectiveness: Compare the cost of repairing versus replacing components to determine which option provides better value for money.
- Availability of replacement parts: Assess the availability of replacement parts for the specific component. Repair might be a more viable choice if they are scarce or expensive.
Sometimes, it may be necessary to consult a professional technician to diagnose the issue and accurately recommend the most suitable action.
Keep the Upper Hand in the War Against Silent PC Killers with XOrca’s Computer Consultants
Now that you know the hidden dangers of silent PC killers, taking proactive measures to protect your hardware systems is crucial. With XOrca, you can stay one step ahead in this battle and safeguard your business from potential threats.
XOrca offers comprehensive security solutions to detect and neutralize silent PC killers before they wreak havoc on your systems. By implementing XOrca’s advanced monitoring and threat detection capabilities, you can ensure your hardware remains secure and operational.
Don’t wait for disaster to strike – take action now! Investing in professional IT support, like XOrca, can save you valuable time, money, and headaches. Protecting your business from silent PC killers is not just a luxury; it’s necessary in today’s digital landscape. So why leave your systems vulnerable when there are practical solutions available?
Take control of your hardware security today with XOrca Computer Consultants and enjoy peace of mind knowing you have a powerful defense against silent PC killers.


0 Comments